Microsoft has revealed it has detected a comprehensive network of cyberattacks originating from North Korea. The hacking group has been dubbed Thallium, and it is the fourth nation-state group Microsoft has identified deploying malicious cyberactivity, following Russia, China and Iran.
Microsoft’s Corporate Vice President of Customer Security & Trust Tom Burt outlines how a recent court order enabled the company to take control of 50 domains that have been linked to malicious cyberactivity. Burt claims Thallium has been using a technique called spear-phishing, stealing sensitive information from a number of victims, including government employees and individuals working on nuclear proliferation issues.
The technique involves emails designed to trick victims into clicking malicious links from which either their log-in details are stolen, or their system is infected with malware. The majority of targets identified were in the US, Japan or South Korea.
“By gathering information about the targeted individuals from social media, public personnel directories from organizations the individual is involved with and other public sources, Thallium is able to craft a personalized spear-phishing email in a way that gives the email credibility to the target,” Burt explains before offering a specific example of one of the phishing emails. “… the content is designed to appear legitimate, but closer review shows that Thallium has spoofed the sender by combining the letters “r” and “n” to appear as the first letter “m” in “microsoft.com.”
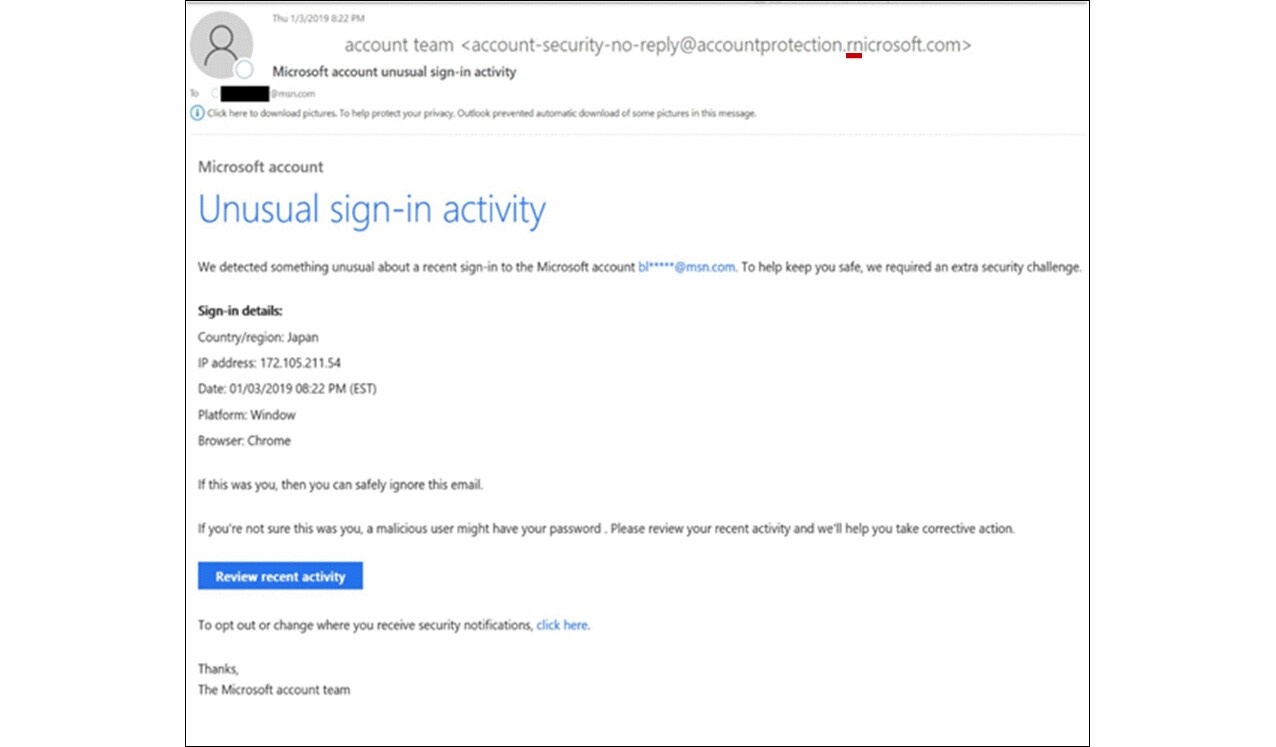
While this form of phishing using fake email addresses is an old hacker strategy, it undoubtedly works. And Burt stresses this is now the fourth major nation-state group using this tactic to target specific victims that Microsoft has disrupted.
“Previous disruptions have targeted Barium, operating from China, Strontium, operating from Russia, and Phosphorus, operating from Iran,” Burt writes. “These actions have resulted in the takedown of hundreds of domains, the protection of thousands of victims and improved the security of the ecosystem.”
Russian hacking group Strontium, also known as Fancy Bear, has on several occasions been detected using this kind of tactic to target US government officials. Microsoft has previously reported taking over phishing domains including “senate.group” and “adfs-senate.email”. These actions were detected during both the 2016 US Presidential election and the 2018 US mid-term elections.
Source: Microsoft