What if someone could take control of an autonomous car simply by playing a piece of music embedded with malicious sound frequencies? Researchers at the University of Michigan have provided compelling evidence highlighting how a variety of technologies including smartphones, fitness wearables and automobiles can be hacked using specific acoustic tones.
An incredible array of devices we use every day rely on internal sensors that read and react to their surroundings in real time. These technologies are known as Microelectromechanical systems (MEMS) and the capacitive MEMS accelerometer is one of the more widely used sensing systems. It's found in many modern gadgets, from implantable medical devices to crucial industrial systems and consumer gadgets.
A University of Michigan team discovered that by deploying precisely tuned acoustic tones, these accelerometers could be fooled into registering false movement readings. These false readings could be so precisely calibrated that they enabled the researchers to take control of some of these devices.
"The fundamental physics of the hardware allowed us to trick sensors into delivering a false reality to the microprocessor," explains Associate Professor of Computer Science and Engineering Kevin Fu.
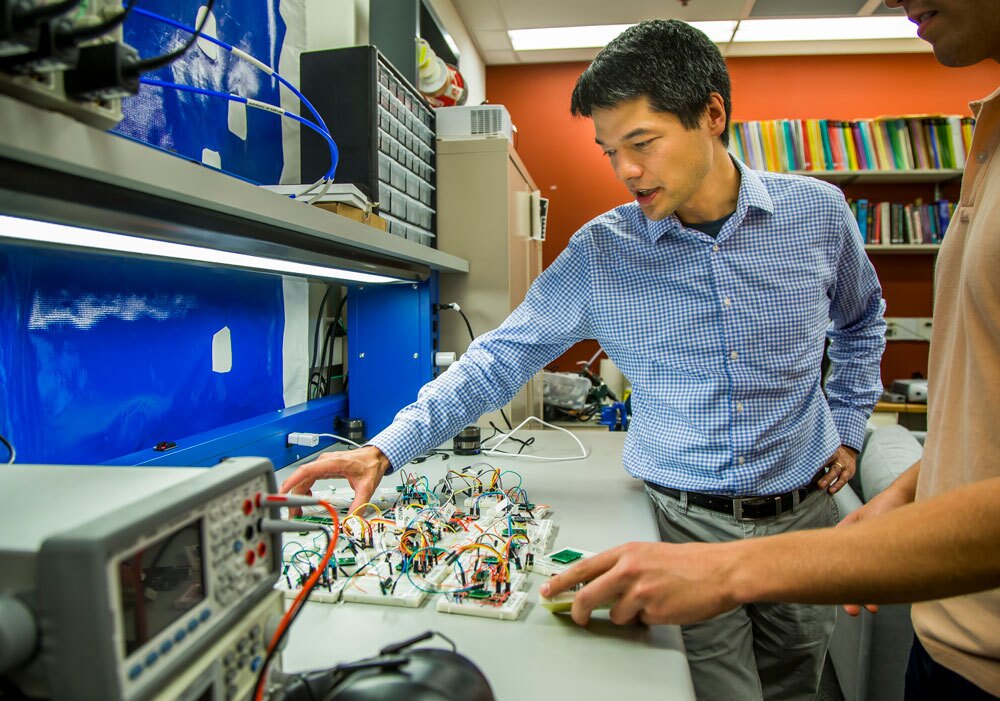
The team's study demonstrated several ways devices could be exploited and controlled through acoustic waves. On the more innocuous end of the spectrum, they played acoustic tones out of a cheap speaker causing a Fitbit to register thousands of fictitious steps. The team noted that several major companies offer rewards programs that tether to a user's Fitbit and they even joined one of the programs and earned rewards points related to the fictitious steps generated by their acoustic hacks.
The more interesting, and potentially dangerous, display of the security exploit came when the team took control of an RC car by attacking the smartphone that was directing it. They took an Android phone that was using an application that directed the RC car based on the phone's orientation, which was measured by the phone's MEMS accelerometer. They then created a music file that could spoof the accelerometer into sending false data to the RC car directing it to move forwards and backwards.
Even more startling was the fact that they had the malicious audio file play from the same audio device that was controlling the RC car. This illustrates how a device could essentially hack itself simply through audio waves disrupting internal sensors.
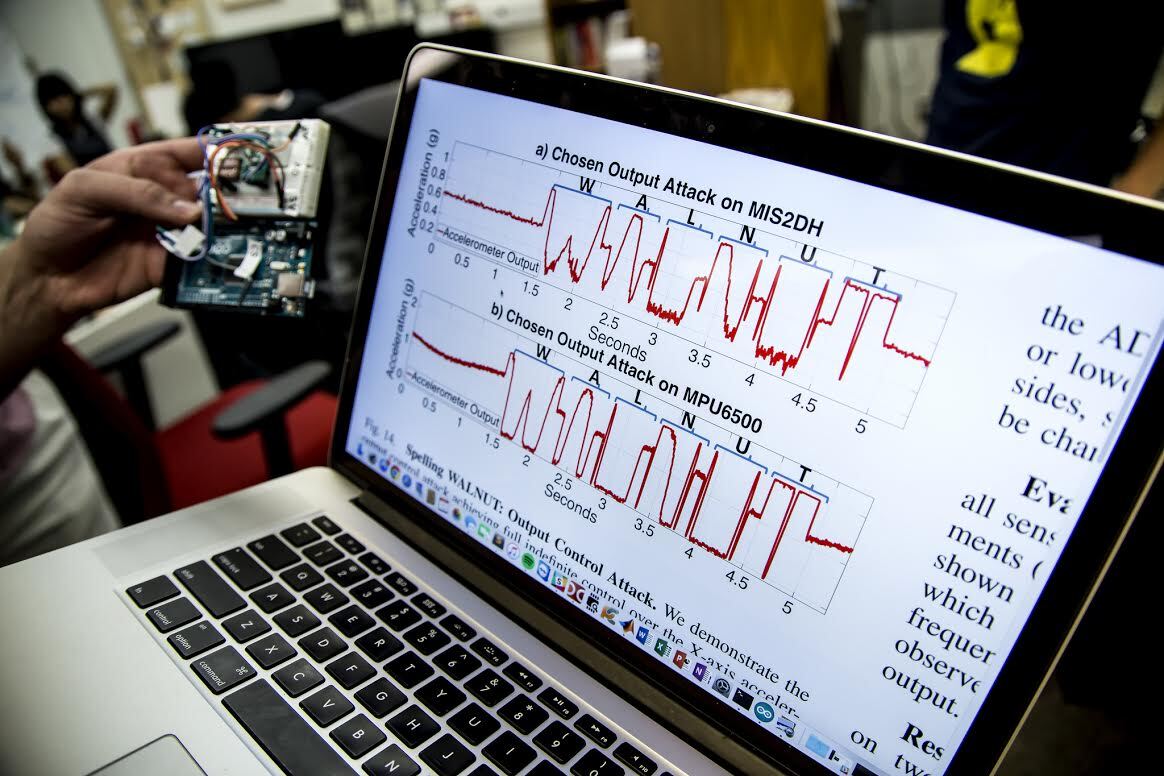
While this is a long way from offering a practical way that autonomous cars could be hacked by someone simply standing on the street with a boombox, the researchers do warn of the dangers in having software rely on data fed from sensors that could easily be manipulated.
"Thousands of everyday devices already contain tiny MEMS accelerometers," Fu points out. "Tomorrow's devices will aggressively rely on sensors to make automated decisions with kinetic consequences."
The researchers offer several potential ways to manage these problems, from adjustments in hardware design to a couple of low-cost software options that could limit a device's vulnerability to these acoustic attacks.
The team will present their paper later in April at the IEEE European Symposium on Security and Privacy and explain their work in detail in the video below.
Source: University of Michigan