Cybersecurity
-
An underreported proposal from the US government could see the sale and import of connected vehicle components prohibited if they're linked to China or Russia. The rule could have far-reaching effects, but it seems motorcyclists might feel it first.
-
Cybersecurity is a growing concern as more critical infrastructure can be exposed to hacks. Now Australian engineers have developed and demonstrated a new technique called “ineffable cryptography,” which treats keys like the Coca-Cola secret formula.
-
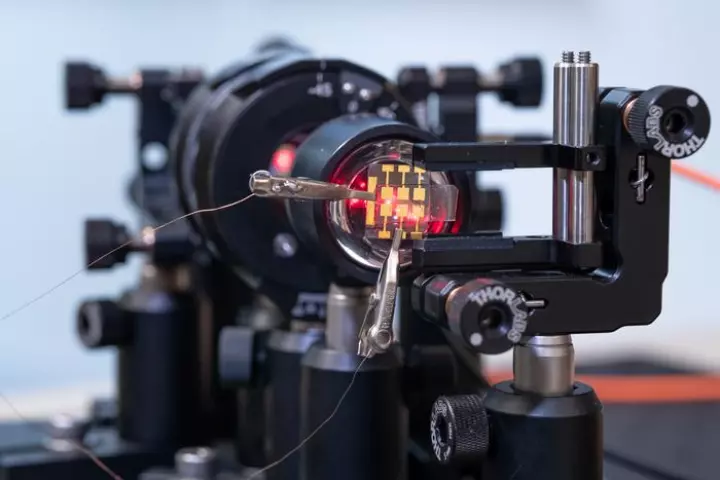
Random numbers are critical to encryption algorithms, but they're nigh-on impossible for computers to generate. Now, Swedish researchers say they've created a new, super-secure quantum random number generator using cheap perovskite LEDs.
-
Why has a major cyber warfare power like Russia launch so few and such ineffective cyber attacks against Ukraine and its sympathizers? New Atlas looks into the digital battle for Ukraine and its implications for the future.
-
IBM security analysts have discovered a global phishing campaign designed to infiltrate organizations associated with managing cold chain supplies of COVID-19 vaccines. The analysis suggests this campaign bears the hallmarks of nation-state spycraft.
-
Every year, the Bulletin of the Atomic Scientists updates the status of its Doomsday Clock. The closer to midnight that the minute hand moves, the bigger the threat of catastrophe. And the 2020 clock is the most dire warning to date.
-
Lockheed Martin, the Missile Defense Agency and the USAF connected an F-35, U-2 spy-plane, and a ground station as part of a missile defense exercise.
-
In an expansive submission to the Australian Parliament, Apple has strongly condemned the government’s prospective anti-encryption legislation, arguing “this is no time to weaken encryption,” and calling the draft outline “extraordinarily broad” and “dangerously ambitious.”
-
IBM Research has released its annual “5 in 5” list, outlining five technologies that the company believes will be instrumental over the next five years. This year’s list focuses on security and AI, predicting that by 2023 we’ll have unhackable encryption, unbiased AI and mainstream quantum computers
-
Cyberwarfare is a growing problem, with 2017 seeing some of the most devious attacks ever. As part of a US$50-million DARPA program to improve cybersecurity, computer scientists at the University of Michigan are developing a security system baked into the hardware that's said to be “unhackable.”
-
As Tuesday’s ransomware attack continues to spread, several security analysts are saying that this virus may not be ransomware after all, but is actually a cyberattack in disguise.
-
Raytheon will use the 2017 Paris Air Show to showcase the technologies it is developing to provide defenses and countermeasures in the new battleground of cyberspace.
Load More